Router Configuration Standards Physical Security The most basic and most important aspect of protecting a router from unauthorized access is physical security. Anyone with physical access to the router can gain control over it, whether through an unprotected port or by more disruptive methods (performing a password recovery). Therefore, it is vitally important to prevent...
Switch Configuration Standards VLAN 1 and Switch Management Switched networks employ several control protocols that work to ensure the smooth flow of user data across the network. This section discusses significance VLAN 1 and its relevance to switch control protocols used in switched network environment. The section also establishes the Organization’s standards for configuring a...
If users recently changed their network passwords as part of an Active Directory policy, it’s possible the password hasn’t been changed in other applications where the policy is pushed (Exchange/Outlook, Lync Messenger, and any other applications) and will cause lockouts for the account leading to headaches. A good practice if this happens often is to clear out...
If copying/pasting inside of Windows ceases to fail for you, it might be because your clipboard is full. Use this east shortcut to clear your Windows clipboard when you face this issue. Right-click your desktop and create a 'new shortcut'Paste the following command cmd.exe /c “echo off | clip”Name the shortcut.
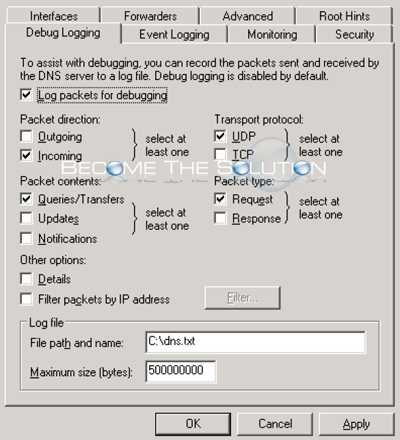
DNS logs are extremely useful for many purposes. Let's review the basic DNS resource records and their purposes. Host address (A). Maps a Domain Name System (DNS) domain name to an Internet Protocol (IP) address that is used by a computer.Alias canonical (CNAME). Maps an alias DNS domain name to another primary name or canonical name.Mail...