Overview Network devices within the enterprise should maintain a consistent, easy-to-understand, format that includes logical, physical, and functional descriptions. Four labels are required when naming the physical chassis of a device to which this standard applies.Floor (optional); device class and number; and logical location and number.Regional code.Top level domain.Five labels are required when naming network interfaces...
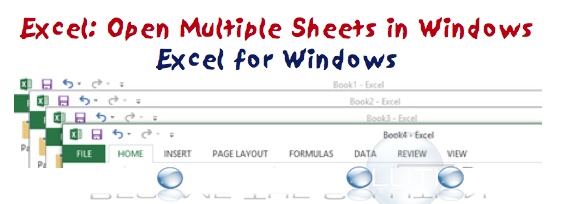
If you are trying to edit multiple Microsoft Excel files, Excel will typically open multiple spreadsheets in a single window. This makes is extremely difficult to toggle between the multiple spreadsheets while work. Below are steps for any version of Microsoft Office to have multiple Excel application windows open for any amount of spreadsheets. 1. ...
Darik’s Boot and Nuke (DBAN) is a utility to securely wipe media hardware – typically hard drives. The utility is used mostly with Windows based systems as it provides a bootable ISO that can be run from USB or a CD. From DBAN’s website:
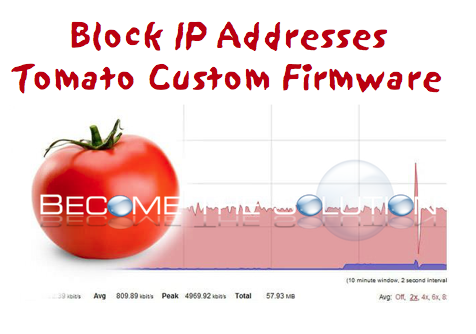
If you custom upgraded your router firmware for Tomato, you might need to take advantage of the iptables Firewall scripts to block incoming IP addresses. You can input any the following commands to block a single or a range of IP addresses. iptables -I FORWARD -s 10.0.0.0/255.0.0.0 -j DROP | Block IP’s 10.0.0.1 – 10.255.255.254...
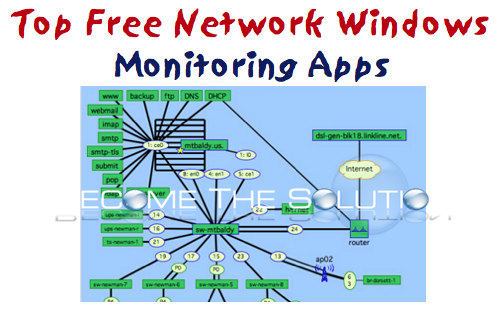
1. WireShark WireShark is one of the most powerful network monitoring and inspection tools available. It provides packet captures and analysis capabilities of a specific network interface on a host. Once you run and collect your packets, you can export them for analysis in another application or use WireShark’s built-in filter to inspect protocols and packet...