How to Setup 802.1 x Authentication Cisco Windows Device
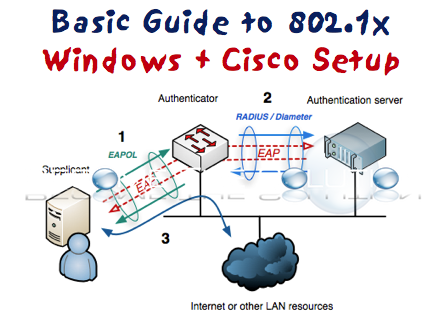
This guide will demonstrate how to configure IEEE 802.1x authentication on switch ports throughout the enterprise by leveraging Microsoft’s Network Policy Server (NPS) as an authenticator to Active Directory. The steps found in this document serve as implementation and diagnostic steps for implementing IEEE 802.1x port authentication across an enterprise network and provides configuration examples for the various devices found on an enterprise network.
1. Configuring Network Policy Server Network Policy Server (NPS), by Microsoft, is used in an enterprise implementation of 802.1x as the proxy to Active Directory. NPS permits flexible configuration using numerous groups for each type of authentication method (MAB, dot1x, etc.).
Launch the NPS administration GUI, then following the steps below to add a new RADIUS client that will be used to authenticate against NPS.
Right-click on “RADIUS Clients” and select “New”.
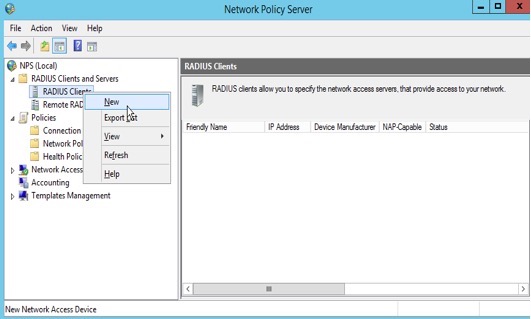
2. Add a RADIUS client using it’s hostname as the “Friendly name”, the IP address, and a shared secret.
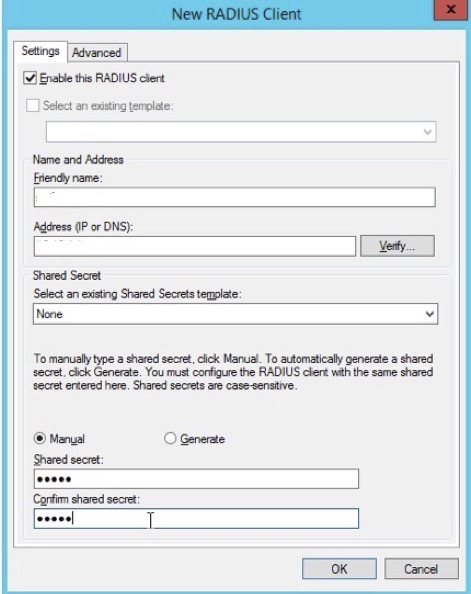
3. Click "Ok"
Configure RADIUS for MAC Authentication Bypass
The following steps show a sample configuration being added for MAC Authentication Bypass (MAB). This configuration is used for VOIP phones to reduce the administrative burden of loading certificates on each phone. MAB uses the phones MAC address as the username and password (both in lowercase). The username should be added to an Active Directory group (in this case, the Windows Group is named “LOC\xxxxx”.
1. Expand the NPS “Policies” tab in the NPS administration GUI, then right-click “Network Policies” to add a new NPS policy.
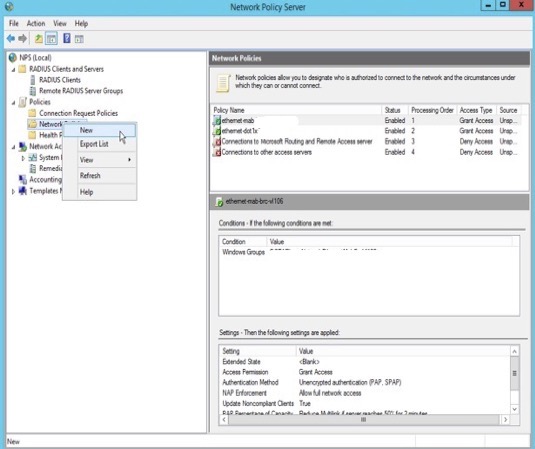
2. Add the name of a new policy in the “Policy name” field, then click “Next”.
3. Next, we will add a condition to permit authentication against this NPS policy using a Windows group.
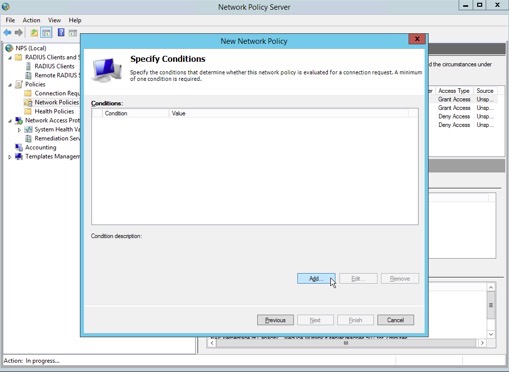
4. Select “Windows Groups” as a condition, then click “Add”.
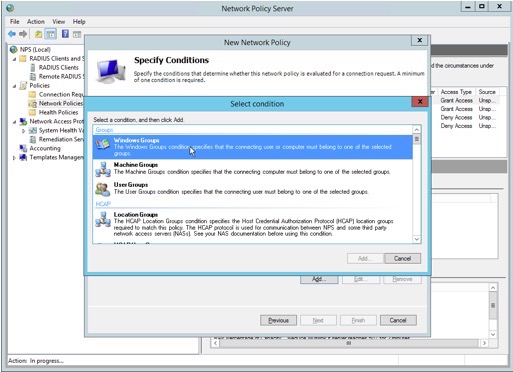
5. Click "Add Groups"
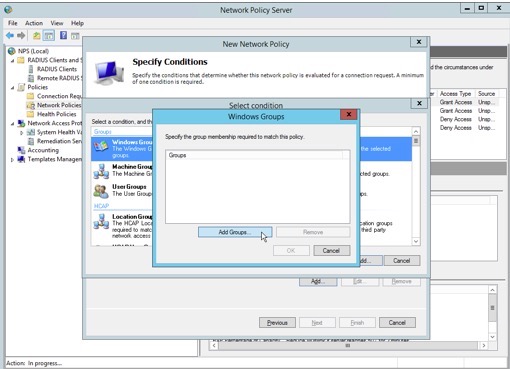
6. Type the name of the Active Directory group, then click “Check Names”. Once that is complete, click “OK”.
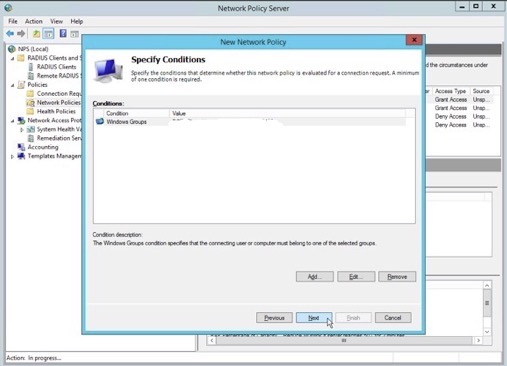
7. Verify the Windows Groups added to this policy entry, then click “OK”.
8. Continue to next screen hit "Next"
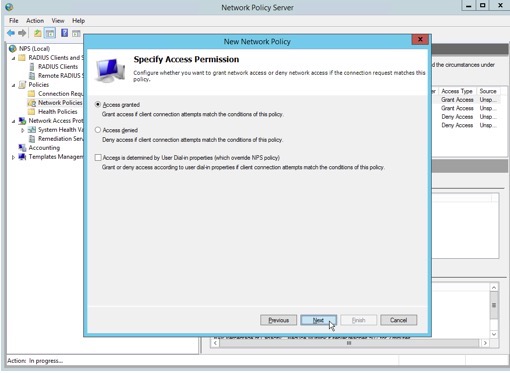
9. Specify access permission as “Access granted”. This permits access to the network.
10. De-select all authentication methods except for “Unencrypted authentication (PAP, SPAP), then click “Next”.
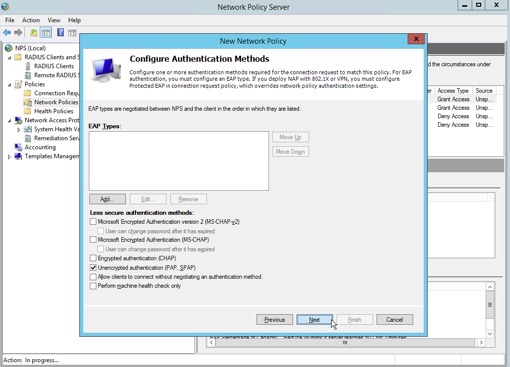
11. NPS prompts the administrator to confirm the use of PAP/SPAP. Click “No” to dismiss the pop-up window and bypass the Help Topic.
12. Remove the “Service-Type” in the following screen.
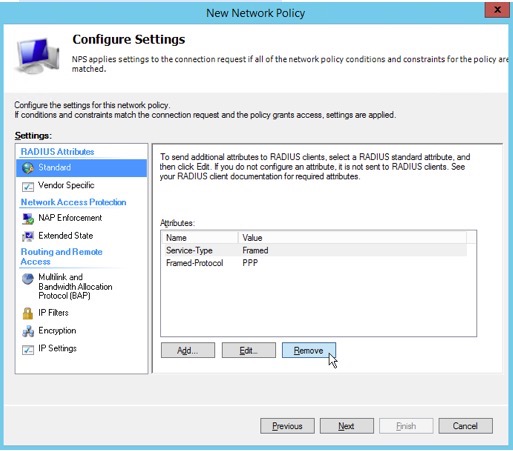
11. Remove the “Framed-Protocol”, then click “Next”.
12. Highlight the “Vendor Specific” tab in the RADIUS Attributes pane, then click “Add” to add an attribute.
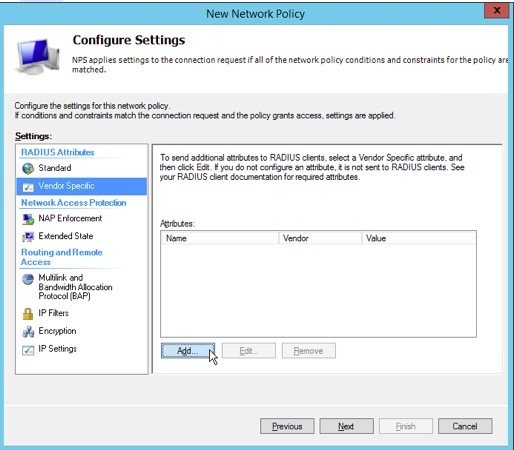
13. Choose “Cisco” from the “Vendor” drop-down selection box.
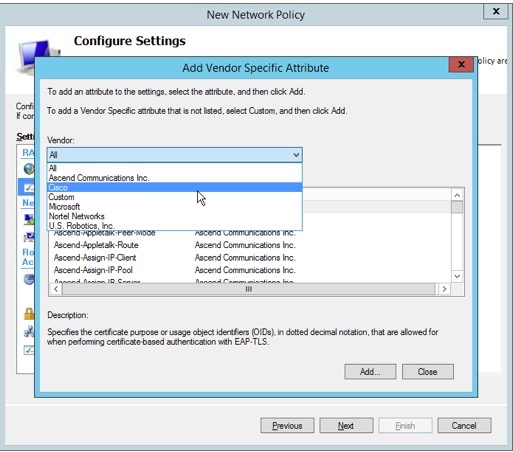
15. Highlight “Cisco-AV-Pair” in the “Attributes” pane, then click “Add”.
16. Click “Add” to create a vendor-specific attribute value used to assign VOIP phones to a voice VLAN.
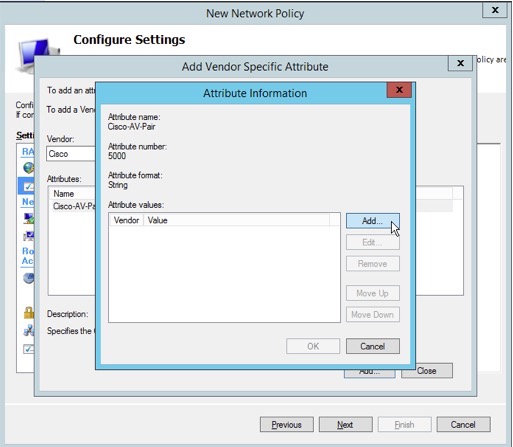
17. Add the string “device-traffic-class=voice” as an Attribute value, then confirm by clicking “OK” twice, and then “Close”.
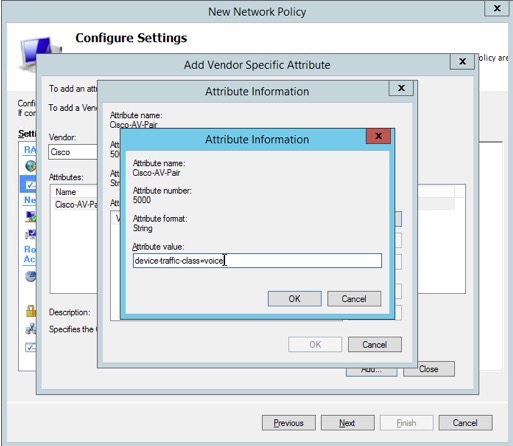
18. Verify that the attribute name “Cisco-AV-Pair” “Cisco” as Vendor and “device-traffic-class=voice” as Value, then click “Next”.
19. Verify the configuration of the new network policy is similar to the following screenshot, then click “Finish”.
20. The network policy is complete. Users that are in the Windows group added to the policy will be able to authenticate using MAC Authentication Bypass, and the switch will configure the port to place the device in the appropriate voice VLAN.
Configure RADIUS to Authenticate Using Protected EAP
The figures below show a summary of configuring Protected Extensible Authentication Protocol (PEAP) in a policy for users in a sample Windows group. This configuration also assigns the switch port to the VLAN labeled “TC_AX_LOC” on the switch. Note: only use descriptive names of switch ports in RADIUS policies; do not use specific VLAN numbers.
1. Policy overview showing that the policy is enabled, access is granted, and the type of network access server is unspecified.
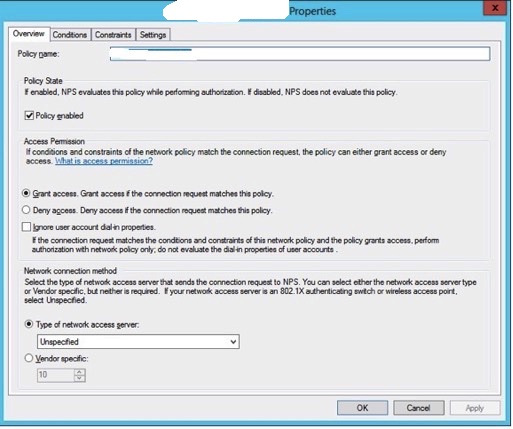
2. The conditions matching this policy entry. A single Windows group is permitted in this policy.
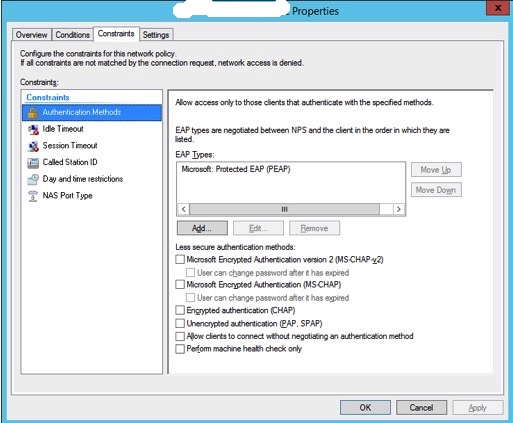
3. The authentication method used is EAP, with only “Microsoft: Protected EAP (PEAP) allowed”.
4. The RADIUS standard attributes required (Framed-Protocol, Service-Type, Tunnel-Medium-Type, Tunnel-Pvt-Group-ID, and Tunnel-Type).
Cisco IOS Configurations
The initial configuration to enable IEEE 802.1x, or “dot1x”, requires several changes to the global configuration context of each switch. These changes affect the behavior of the switch by (1) enabling dot1x system authentication, (2) enabling device tracking to ensure port-hopping attempts are recognized by the device and appropriate action is taken, and (3) enabling the appropriate Authentication, Authorization, and Accounting (AAA) authentication and authorization groups that modify the VLAN assignments of each port as they become authenticated/unauthenticated.
Configure RADIUS Servers
RADIUS servers are configured in the global context with the necessary credentials to proxy authentication requests from the end-station. Each switch should have a unique key implemented in the following stanza.
Configure RADIUS Server Attributes
Several attributes that affect the RADIUS protocol between the switch and RADIUS servers are required to successfully implement dot1x.
Enable Device Tracking
Device tracking ensures port-hopping attempts by a malicious user are recognized by the switch.
1. Configuring Network Policy Server Network Policy Server (NPS), by Microsoft, is used in an enterprise implementation of 802.1x as the proxy to Active Directory. NPS permits flexible configuration using numerous groups for each type of authentication method (MAB, dot1x, etc.).
Launch the NPS administration GUI, then following the steps below to add a new RADIUS client that will be used to authenticate against NPS.
Right-click on “RADIUS Clients” and select “New”.

2. Add a RADIUS client using it’s hostname as the “Friendly name”, the IP address, and a shared secret.

3. Click "Ok"
Configure RADIUS for MAC Authentication Bypass
The following steps show a sample configuration being added for MAC Authentication Bypass (MAB). This configuration is used for VOIP phones to reduce the administrative burden of loading certificates on each phone. MAB uses the phones MAC address as the username and password (both in lowercase). The username should be added to an Active Directory group (in this case, the Windows Group is named “LOC\xxxxx”.
1. Expand the NPS “Policies” tab in the NPS administration GUI, then right-click “Network Policies” to add a new NPS policy.

2. Add the name of a new policy in the “Policy name” field, then click “Next”.
3. Next, we will add a condition to permit authentication against this NPS policy using a Windows group.

4. Select “Windows Groups” as a condition, then click “Add”.

5. Click "Add Groups"

6. Type the name of the Active Directory group, then click “Check Names”. Once that is complete, click “OK”.
7. Verify the Windows Groups added to this policy entry, then click “OK”.
8. Continue to next screen hit "Next"

9. Specify access permission as “Access granted”. This permits access to the network.

10. De-select all authentication methods except for “Unencrypted authentication (PAP, SPAP), then click “Next”.

11. NPS prompts the administrator to confirm the use of PAP/SPAP. Click “No” to dismiss the pop-up window and bypass the Help Topic.
12. Remove the “Service-Type” in the following screen.

11. Remove the “Framed-Protocol”, then click “Next”.
12. Highlight the “Vendor Specific” tab in the RADIUS Attributes pane, then click “Add” to add an attribute.

13. Choose “Cisco” from the “Vendor” drop-down selection box.

15. Highlight “Cisco-AV-Pair” in the “Attributes” pane, then click “Add”.
16. Click “Add” to create a vendor-specific attribute value used to assign VOIP phones to a voice VLAN.

17. Add the string “device-traffic-class=voice” as an Attribute value, then confirm by clicking “OK” twice, and then “Close”.

18. Verify that the attribute name “Cisco-AV-Pair” “Cisco” as Vendor and “device-traffic-class=voice” as Value, then click “Next”.
19. Verify the configuration of the new network policy is similar to the following screenshot, then click “Finish”.
20. The network policy is complete. Users that are in the Windows group added to the policy will be able to authenticate using MAC Authentication Bypass, and the switch will configure the port to place the device in the appropriate voice VLAN.
Configure RADIUS to Authenticate Using Protected EAP
The figures below show a summary of configuring Protected Extensible Authentication Protocol (PEAP) in a policy for users in a sample Windows group. This configuration also assigns the switch port to the VLAN labeled “TC_AX_LOC” on the switch. Note: only use descriptive names of switch ports in RADIUS policies; do not use specific VLAN numbers.
1. Policy overview showing that the policy is enabled, access is granted, and the type of network access server is unspecified.

2. The conditions matching this policy entry. A single Windows group is permitted in this policy.
3. The authentication method used is EAP, with only “Microsoft: Protected EAP (PEAP) allowed”.

4. The RADIUS standard attributes required (Framed-Protocol, Service-Type, Tunnel-Medium-Type, Tunnel-Pvt-Group-ID, and Tunnel-Type).
Cisco IOS Configurations
The initial configuration to enable IEEE 802.1x, or “dot1x”, requires several changes to the global configuration context of each switch. These changes affect the behavior of the switch by (1) enabling dot1x system authentication, (2) enabling device tracking to ensure port-hopping attempts are recognized by the device and appropriate action is taken, and (3) enabling the appropriate Authentication, Authorization, and Accounting (AAA) authentication and authorization groups that modify the VLAN assignments of each port as they become authenticated/unauthenticated.
Configure RADIUS Servers
RADIUS servers are configured in the global context with the necessary credentials to proxy authentication requests from the end-station. Each switch should have a unique key implemented in the following stanza.
| radius-server host X.X.X.X key radius-server host X.X.X.X key |
Several attributes that affect the RADIUS protocol between the switch and RADIUS servers are required to successfully implement dot1x.
| radius-server attribute 6 on-for-login-auth radius-server attribute 8 include-in-access-req radius-server attribute 25 access-request include radius-server vsa send accounting radius-server vsa send authentication |
Enable Device Tracking
Device tracking ensures port-hopping attempts by a malicious user are recognized by the switch.
| ip device tracking |
Enable 802.1x System Authentication and Supplicant Control
The IEEE 802.1x framework requires that `system-auth-control’ be implemented in the global context. We also implement the `guest-vlan’ configuration here should guest VLANs be implemented in the future.
AAA Server Group Configuration
AAA should be configured for dot1x and network authentication, authorization, and accounting to a specific set of servers used for dot1x control. Note: we have selected the group name “RADIUS_SERVERS_B” as the name “RADIUS_SERVERS_A” is reserved for future implementation of RADIUS authentication for administrative device functions.
AAA Default Group Configuration
Finally, add the AAA group configured in the previous section to the global AAA configuration for dot1x/network control.
Interface Configuration
Multi-domain vs. Multi-host Modes
Ports that are configured in multi-domain mode permit devices to be placed on the data VLAN (either statically through an interface statement or by using RADIUS to dynamically assign the port to a VLAN) or voice VLAN. Multi-domain ports should be used on devices that have the ability to act as a bridge by offering a pass-through port for network access. The Avaya 9620 phones in use at the Bank do offer such a feature. Multi-host modes permit multiple hosts per port to be configured on data VLANs and is used when a aggregating several devices into a single switch port (most likely through a downstream switch). Although Cisco offers single-host configurations, limiting the configurations to either multi-domain or multi-host modes reduces the complexity in configuration and troubleshooting.
Wake-on-LAN
Wake-on-LAN (WOL) is fully supported in the switch configurations below. WOL packets do not require authentication when being sent from an upstream device to a switch port that is not currently authenticated. The authentication process will occur when the device “wakes up”, or becomes active.
Voice-Over-IP (VOIP)/Mixed-Use Switchports
Switch interfaces hosting VOIP phones require the continued use of a voice VLAN number assigned by the switch. Voice VLANs cannot be assigned by a RADIUS server in the way a data VLAN is.
Data-Only Switchports
Interfaces hosting devices such as WYSE clients, printers, etc., have their VLAN assignment dynamically configured by RADIUS. These ports are placed into “multi-host” mode which permits more than one MAC address per port which still enforcing dot1x control.
Windows Device Configuration
Authenticating WYSE clients against the NPS configuration PEAP requires several configuration variables to be added to device configurations.
Sample Windows Device Configuration
The IEEE 802.1x framework requires that `system-auth-control’ be implemented in the global context. We also implement the `guest-vlan’ configuration here should guest VLANs be implemented in the future.
| dot1x system-auth-control dot1x guest-vlan supplicant authentication mac-move permit |
AAA Server Group Configuration
AAA should be configured for dot1x and network authentication, authorization, and accounting to a specific set of servers used for dot1x control. Note: we have selected the group name “RADIUS_SERVERS_B” as the name “RADIUS_SERVERS_A” is reserved for future implementation of RADIUS authentication for administrative device functions.
| aaa group server radius RADIUS_SERVERS_B server X.X.X.X auth-port 1645 acct-port 1646 server X.X.X.X auth-port 1645 acct-port 1646 ip radius source-interface Loopback0 |
AAA Default Group Configuration
Finally, add the AAA group configured in the previous section to the global AAA configuration for dot1x/network control.
| aaa authentication dot1x default group RADIUS_SERVERS_B aaa authorization network default group RADIUS_SERVERS_B aaa accounting network default start-stop group RADIUS_SERVERS_B aaa accounting dot1x default start-stop group RADIUS_SERVERS_B |
Interface Configuration
Multi-domain vs. Multi-host Modes
Ports that are configured in multi-domain mode permit devices to be placed on the data VLAN (either statically through an interface statement or by using RADIUS to dynamically assign the port to a VLAN) or voice VLAN. Multi-domain ports should be used on devices that have the ability to act as a bridge by offering a pass-through port for network access. The Avaya 9620 phones in use at the Bank do offer such a feature. Multi-host modes permit multiple hosts per port to be configured on data VLANs and is used when a aggregating several devices into a single switch port (most likely through a downstream switch). Although Cisco offers single-host configurations, limiting the configurations to either multi-domain or multi-host modes reduces the complexity in configuration and troubleshooting.
Wake-on-LAN
Wake-on-LAN (WOL) is fully supported in the switch configurations below. WOL packets do not require authentication when being sent from an upstream device to a switch port that is not currently authenticated. The authentication process will occur when the device “wakes up”, or becomes active.
Voice-Over-IP (VOIP)/Mixed-Use Switchports
Switch interfaces hosting VOIP phones require the continued use of a voice VLAN number assigned by the switch. Voice VLANs cannot be assigned by a RADIUS server in the way a data VLAN is.
| switchport mode access switchport voice vlan authentication host-mode multi-domain authentication port-control auto authentication periodic authentication event fail action next-method authentication control-direction in ; permit Wake-on-LAN dot1x pae authenticator mab authentication order dot1x mab authentication priority dot1x mab |
Data-Only Switchports
Interfaces hosting devices such as WYSE clients, printers, etc., have their VLAN assignment dynamically configured by RADIUS. These ports are placed into “multi-host” mode which permits more than one MAC address per port which still enforcing dot1x control.
| switchport mode access authentication host-mode multi-host authentication port-control auto authentication periodic authentication event fail action next-method authentication control-direction in ; permit Wake-on-LAN dot1x pae authenticator authentication order dot1x authentication priority dot1x |
Windows Device Configuration
Authenticating WYSE clients against the NPS configuration PEAP requires several configuration variables to be added to device configurations.
| Variable |
Value Required |
Description |
| IEEE8021x |
yes |
Initializes the 802.1x framework |
| network |
wired |
Specifies which interface to use 802.1x |
| eap |
yes |
Enables Extensible Auth Protocol on the client |
| eaptype |
EAP-PEAP |
Defines the specific EAP type supported by NPS |
| peapeap |
EAP-MSCHAPV2 |
The PEAP type; MS CHAP version 2 |
| peapidentity |
tc-ax-dot1x. |
Internal reference identity on the client |
| peapmschapun |
tc-ax-dot1x. |
The username provided to the MSCHAPv2 dialog |
| peapmschappwd |
The password provided to the MSCHAPv2 dialog |
|
| peapmschapdm |
A required authentication domain (e.g. enterprise.loc) |
Sample Windows Device Configuration
| IEEE8021x=yes network=wired \ eap=yes eaptype=EAP-PEAP \ peapeap=EAP-MSCHAPV2 \ peapidentity=tc-ax-dot1x. \ peapmschapun=tc-ax-dot1x. \ peapmschappwd=2_many_secrets \ peapmschapdm=enterprise.loc |
* Please use the comment form below. Comments are moderated.*

Comments