Windows DNS Logs Deciphering
DNS logs are extremely useful for many purposes. Let's review the basic DNS resource records and their purposes.
- Host address (A). Maps a Domain Name System (DNS) domain name to an Internet Protocol (IP) address that is used by a computer.
- Alias canonical (CNAME). Maps an alias DNS domain name to another primary name or canonical name.
- Mail Exchanger (MX). Maps a DNS domain name to the name of a computer that exchanges or forwards mail.
Problem:
An organization is migrating their Windows 2008 production file server(s) (active/standby) to a DFS system. The file server had a Host A record created named 'fileserver' mapped to 10.10.39.1.
The problem is many employees are using the A record 'fileserver' in excel, business applications, file drive mappings, and such. Since the business was told to reference this name as needed, there's no telling where the A record could exist exactly - a very bad practice. DFS will be referenced by a global domain name.
Luckily, DNS logs can help an administrator to where 'fileserver' is being referenced on host machines.
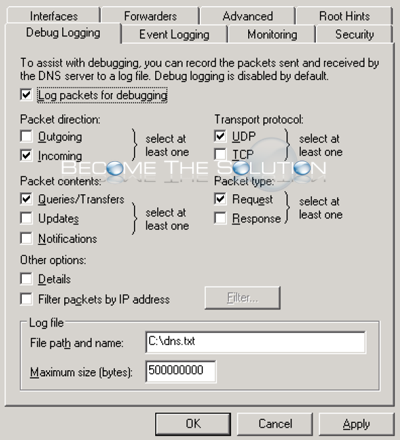
The following example shows the logging options within Windows DNS manager that we're concerned with. Depending how big your organization is, this will capture a lot of information. The log file is overwritten when it reaches the maximum file size. Set this file size with caution.
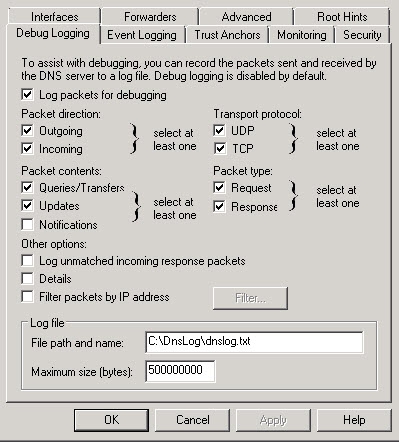
From TechNet: <https://technet.microsoft.com/en-us/library/cc776361(v=ws.10).aspx>
- Direction of packets
Send Packets sent by the DNS server are logged in the DNS server log file.
Receive Packets received by the DNS server are logged in the log file. - Content of packets
Standard queries Specifies that packets containing standard queries (per RFC 1034) are logged in the DNS server log file.
Updates Specifies that packets containing dynamic updates (per RFC 2136) are logged in the DNS server log file.
Notifies Specifies that packets containing notifications (per RFC 1996) are logged in the DNS server log file. - Transport protocol
UDP Specifies that packets sent and received over UDP are logged in the DNS server log file.
TCP Specifies that packets sent and received over TCP are logged in the DNS server log file. - Type of packet
Request Specifies that request packets are logged in the DNS server log file (a request packet is characterized by a QR bit set to 0 in the DNS message header).
Response Specifies that response packets are logged in the DNS server log file (a response packet is characterized by a QR bit set to 1 in the DNS message header). - Enable filtering based on IP address Provides additional filtering of packets logged in the DNS server log file. This option allows logging of packets sent from specific IP addresses to a DNS server, or from a DNS server to specific IP addresses.
- File name Lets you specify the name and location of the DNS server log file.
For example:- dns.log specifies that the DNS server log file should be saved as dns.log in the systemroot\System32\Dns directory.
- temp\dns.log specifies that the DNS server log file should be saved as dns.log in the systemroot\Temp directory
- Log file maximum size limit Lets you set the maximum file size for the DNS server log file. When the specified maximum size of the DNS server log file is reached, the DNS server overwrites the oldest packet information with new information. Note: If left unspecified, the DNS server log file's size can take up a large amount of hard disk space.
Depending on your org size, you should at least capture 1 full business day of DNS logs before reviewing. Once ready, we can easily filter the log file in command prompt.
In this example, the DNS log file resides in a shared network drive. We will find any reference of 'filserver' and output to a text file in same directory.
Open command prompt with Admin privileges if needed.
1. First we will likely have to to store the shared directory in command prompt before we can find in the log. (This step may not be necessary for all)
C:\Users\> pushd \\shared\DnsLog

2. Find references of "fileserver"
Z:\> find "fileserver" /i z:\dnslog.txt > dns

Open the created text file in Excel -> Tab Delimited. Sort by IP addresses and clean up duplicates. IP addresses are great...but host/domain/FQDN's would be best to help identify systems.
Download and open dns-script script. Paste the IP Addresses from excel into the iplist.txt file.
Open fqdn.bat and add your DNS server IP in set server field and save.
Run fqdn.bat and it will create a .cvs output in same directory. Now you should see hostnames associated with your IP's!
DNS Hex Log reference:
|
0x0 |
0 |
No logging. (This is the default) |
|
0x1 |
1 |
Queries transactions |
|
0x10 |
16 |
Notifications transactions |
|
0x20 |
32 |
Updates transactions |
|
0xFE |
254 |
Non-queries transactions |
|
0x100 |
256 |
Question packets |
|
0x200 |
512 |
Answer packets |
|
0x1000 |
4096 |
Send packets |
|
0x2000 |
8192 |
Receive packets |
|
0x4000 |
16384 |
UDP packets |
|
0x8000 |
32768 |
TCP packets |
|
0xFFFF |
65535 |
All packets |
|
0x10000 |
65536 |
AD write transactions |
|
0x20000 |
131072 |
AD update transactions |
|
0x1000000 |
16777216 |
Full packets |

Comments