Terminal & Shell Basics cmd+n – Open a new Shell in a new windowcmd+t – Open a new Shell in a new tab of the current windowcontrol+d – Logout the Shell in the current tab / windowcmd+d – Split pane. this is not a new shell, just a way of displaying the current Shell. System Restart...
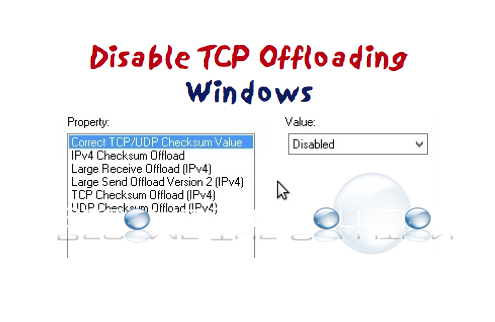
TCP offload engine is a function used in network interface cards (NIC) to offload processing of the entire TCP/IP stack to the network controller. By moving some or all of the processing to dedicated hardware, a TCP offload engine frees the system's main CPU for other tasks. TCP offloading has been known to cause some issues,...
Reference: http://en.wikipedia.org/wiki/Circuit_IDTelecom Circuit ID formats The LEC circuit IDs are based on Telcordia Technologies' Common Language Coding. At one time, the abbreviations were meaningful (for example, HC for high capacity) but the complexity of the business no longer allows for it. Carrier Facility format: AAAAA/BBBBBB/CCCCCCCCCCC/DDDDDDDDDDD[1] A Prefix: 3-5 Alphanumeric characters. Required.B Facility Type: 2–6 Alphanumeric characters. Required.C A CLLI Code: 8 or...
A letter of authorization may aid a person who requires help to perform critical duties in a formal setting. Legally, a letter of authority is sufficient to delegate sensitive legal, health or financial obligation to another person or entity.ISP Providers are required to send a letter of authorization to an organization for access to install a...
Router Configuration Standards Physical Security The most basic and most important aspect of protecting a router from unauthorized access is physical security. Anyone with physical access to the router can gain control over it, whether through an unprotected port or by more disruptive methods (performing a password recovery). Therefore, it is vitally important to prevent...